The lack of HTTPS at Amazon: identifying items purchased using information leakage
April 3, 2015
If you were to browse Amazon right now and someone was eavesdropping on your connection, they could tell exactly what you were looking at. Even if you're logged in, all item browsing takes place over HTTP. This is tremendously odd given that it's 2015 and encryption is well and truly fast enough for the masses...
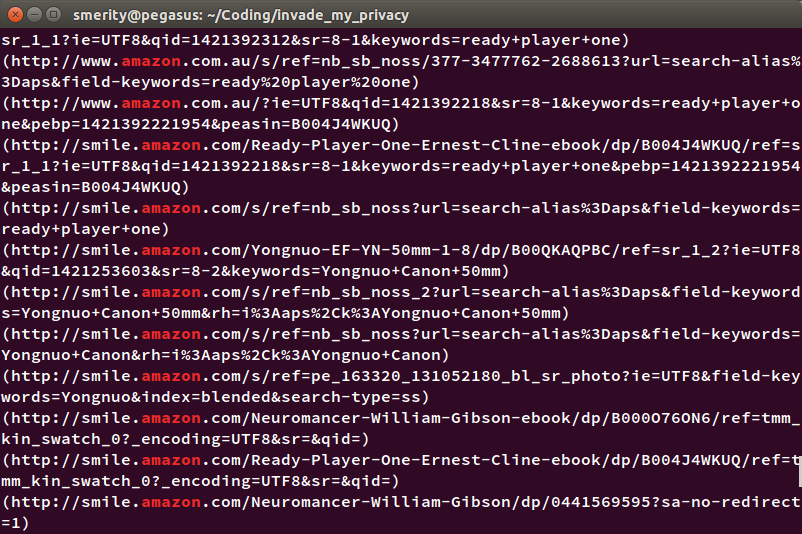
This is a small extract from my browser history, filtered to only contain HTTP URLs. You can see both my searches ("Yongnuo camera lenses") and the individual items I browse (such as the Ready Player One novel).
Whilst that's troubling by itself, that's just the tip of the iceberg. Using trivial HTTP metadata, you can tell which items have been purchased by a user. If you capture the content and perform simple analysis, you can discover additional details such as when it was purchased and what product options were selected.
I reported this to Amazon previously via their security email but received a boilerplate response. Considering anyone interested in utilizing this information leak would already be doing so, I feel it's worth raising awareness about the situation. At the very least, it adds to some of my previous articles on the lack of default HTTPS on Google Analytics and when HTTP referrers appear and disappear.
Discovering which products a user has purchased
When you navigate to your Order History on Amazon, you're redirected to use HTTPS and are required to log in. This prevents anyone from eavesdropping on your connection from trivially seeing what you have purchased.
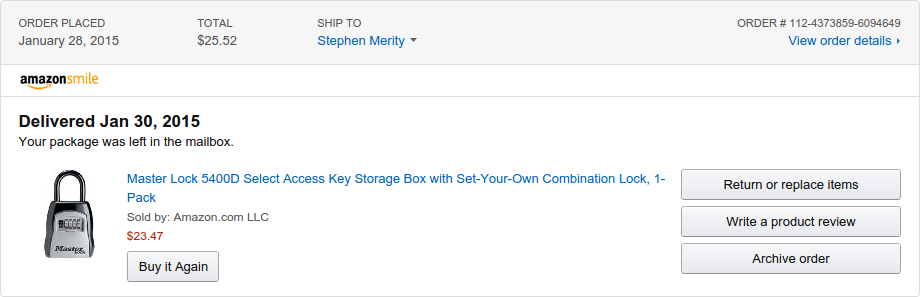
A sample item from my Order History found at https://smile.amazon.com/gp/css/order-history, securely served over HTTPS.
Unfortunately, if you click on any of your purchased items on this page, you are sent to the item page over HTTP, with a referrer added to the the URL, ref=oh_....
The oh stands for Order History and indicates that this item was clicked from your Order History page.
The Order History page does contain cancelled items however, so it's only highly probable that you purchased it. Luckily, Amazon include a little purchase information box that tells me I purchased this lock box on the 28th of January -- specifically the shackle mounted model. This is all over HTTP, for anyone to listen in on.
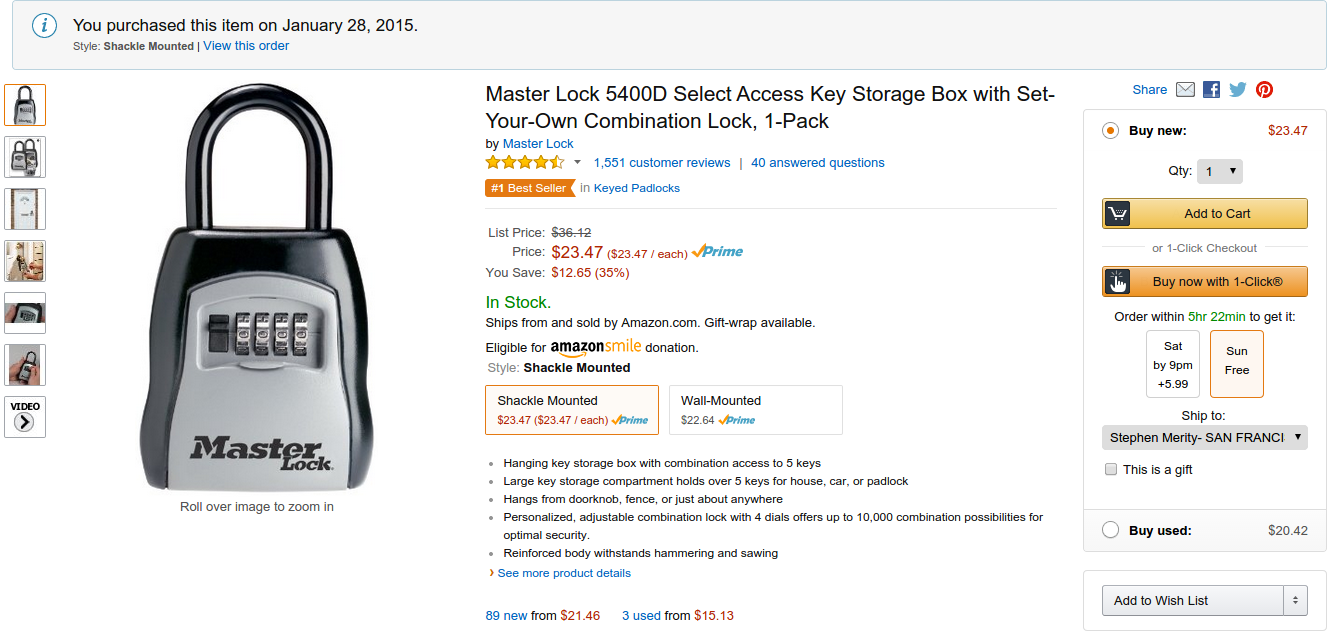
If I browse to this page, the ref=oh_... indicates this item was from the Order History page.
If I browse to this page from anywhere, the purchase information box is provided, and is sent over insecure HTTP.
Amazon could fix some of this by removing the referrer (ref) but that would still leave the product box which appears if the user views the item's page.
Most importantly, leaving pages to be served over HTTP allows for other future information leaks to occur.
The easiest solution would be to sidestep the entire situation and go to HTTPS by default.
The question of whether TLS is fast enough has been answered long ago.
It's 2015 and Amazon is used all over the world. The list of countries they ship to is staggering. Their customers may face threats from something as trivial as an insecure wireless point at a cafe to the extreme of an oppressive government who hold no regards to their privacy. Why not make the world a little more resilient to eavesdropping at the flip of a switch?
Popular Articles
- It's ML, not magic: machine learning can be prejudiced
- It's ML, not magic: the rise of AI-prefix investing
- In deep learning, architecture engineering is the new feature engineering
- How Google Sparsehash achieves two bits of overhead per entry using sparsetable
- Where did all the HTTP referrers go?
Interested in saying hi? ^_^
Follow @Smerity